Azure (Office 365) SSO SAML Integration
A cloud-hosted Azure Active Directory is a service provided by Microsoft that can provide a single sign-on using your Active Directory credentials. PAM supports integration with single sign-on (SSO) logins through a SAML 2.0 identity provider (IDP) like those of Azure AD (AAD) to provide authentication services.
Requirements
Before you begin to integrate PAM with your AAD using SAML, be sure you met the following pre-requisities:
- A working PAM deployment with the Federated Sign-In experience. The PAM Federated Sign-In module provides the required SAML 2.0 web login functionality.
- A working PAM deployment with Active Directory integration. This Active Directory integration provides the security for users and groups in PAM after they are authenticated via AAD.
- Access to your existing PAM host server. You will need to update a configuration file, certificates and restart services.
- The required Azure subscription plan and an account with access to create and configure Non-gallery applications in Azure Active Directory.
Step 1: Create and Configure your Azure AD Enterprise Application
This step describes the process required to create and begin the configuration of your Azure Enterprise Application.
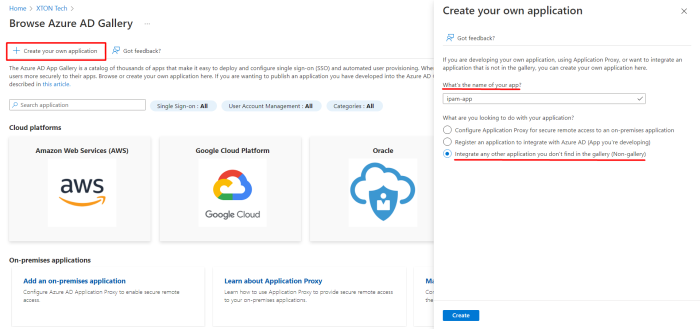
- Login to your Azure Management Portal and navigate to Azure Active Directory > Enterprise Applications and click on the Create your own application button.
-
Enter a new name for your application select Integrate any other application you don't find in the gallery (Non-gallery) and click the Create button.
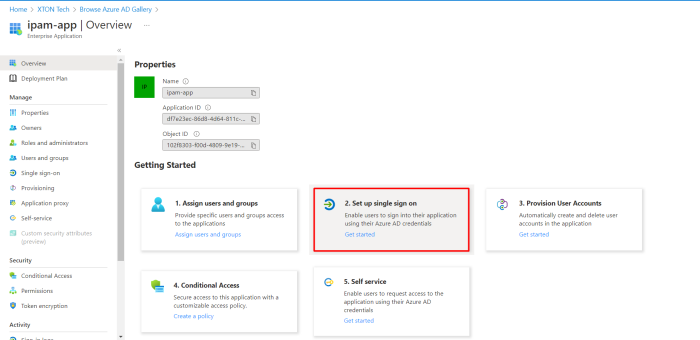
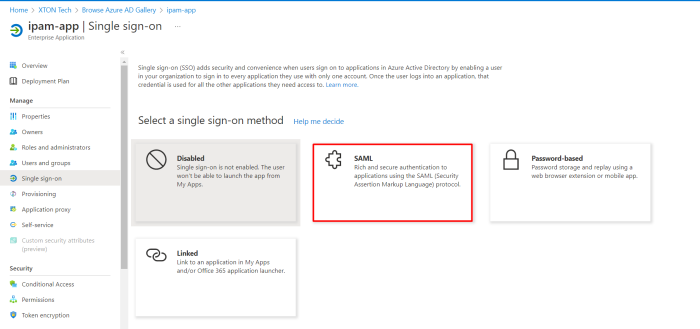
- Once your app is created, navigate Set up single sign-on menu and click the SAML tile.
-
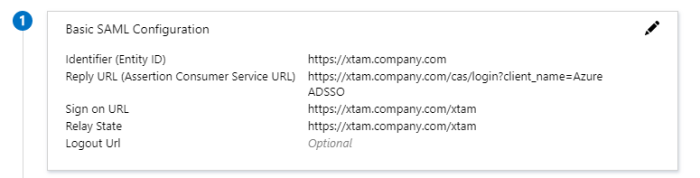
Now we will begin the first part of this app’s SAML configuration. In the Basic SAML Configuration section, click the Edit button (pencil icon) and populate the following parameters:
-
Identifier (Entity ID) (Required) – Enter your PAM host name like https://xtam.company.com
-
Reply URL (Assertion Consumer Service URL) (Required) – Enter your PAM host name plus /cas/login?client_name=AzureSSO. For example, https://xtam.company.com/cas/login?client_name=AzureSSO
-
Sign On URL (Optional) – Enter your PAM login page like https://xtam.company.com/xtam
-
Relay State (Optional) – Enter your PAM login page like https://xtam.company.com/xtam
-
Logout URL (Optional) – leave empty
-
Please do not logout of your Azure Management Portal yet. We will return to this Enterprise Application later to complete the required configuration.
Step 2: Begin Configuration of PAM
This step describes the process required to modify PAM configuration in order to identify your Azure Enterprise Application.
- Login to the PAM server and open the file $PAM_HOME/web/conf/catalina.properties in a text editor.
- Locate the section labeled # CAS and add or update the following lines replacing {cas.managed.path} with your PAM host server like https://xtam.company.com:
-
Below this # CAS section, create a new section with the following lines:
Copy# Azure SSO SAML
cas.authn.pac4j.saml[0].clientName=AzureSSO
cas.authn.pac4j.saml[0].keystorePassword={password}
cas.authn.pac4j.saml[0].privateKeyPassword={keystorePassword}
cas.authn.pac4j.saml[0].serviceProviderEntityId={https://xtam.company.com/xtam/}
cas.authn.pac4j.saml[0].serviceProviderMetadataPath={c:/xtam/content/keys/azuresso.xml}
cas.authn.pac4j.saml[0].keystorePath={c:/xtam/content/keys/samlKeystoreAzureSSO.jks}
cas.authn.pac4j.saml[0].identityProviderMetadataPath={https://login.microsoftonline.com/yourAzureDirectoryID/federationmetadata/2007-06/federationmetadata.xml?appid=yourAzureEnterpriseApplicationID}
cas.authn.pac4j.saml[0].maximumAuthenticationLifetime=2073600 - cas.authn.pac4j.saml[0].clientName=AzurSSO - This parameter will define the button name on the PAM login page for this SAML authentication. We recommend not including spaces in this value.
- cas.authn.pac4j.saml[0].keystorePassword ={password} - Define an alpha-numeric password.
- cas.authn.pac4j.saml[0].privateKeyPassword{keystorePassword} - Define the same alpha-numeric password as the keystorePassword.
- cas.authn.pac4j.saml[0].serviceProviderEntityId={https://pam.company.com/xtam/} - Enter the exact value from your Azure Enterprise Application’s Identifier (Entity ID) as configured in step 1.
- cas.authn.pac4j.saml[0].serviceProviderMetadataPath={azuresso.xml} - Define an PAM path and name that will be used for the Federated Metadata xml file. We recommend storing this file in the $PAM_HOME/content/keys for example c:/pam/content/keys/azuresso.xml (Windows) or /opt/pam/content/keys/azuresso.xml (Linux).
- cas.authn.pac4j.saml[0].keystorePath={samlKeystoreAzureSSO.jks} - Define an PAM path and name for the PAM keystore file (.jks). We recommend storing this file in the $PAM_HOME/content/keys for example $PAM_HOME/content/keys/samlKeystoreAzureSSO.jks (Windows) or /opt/pam/content/keys/samlKeystoreAzureSSO.jks (Linux) *or c:/xtam/content/keys/samlKeystoreAzureSSO.jks (Windows) or /opt/xtam/content/keys/samlKeystoreAzureSSO.jks (Linux) for the long time users.
- cas.authn.pac4j.saml[0].identityProviderMetadataPath={path} - Enter the entire URL from your Azure Enterprise Application’s App Federation Metadata URL. The URL should resemble this format: https://login.microsoftonline.com/yourAzureDirectoryID/federationmetadata/2007-06/federationmetadata.xml?appid=yourAzureEnterpriseApplicationID
- cas.authn.pac4j.saml[0].maximumAuthenticationLifetime=2073600: This value defines a 24 day period (value in seconds) in which a user has generated a last authentication event in Azure Active Directory. This parameter helps if users begin experiencing login issues due to old Azure authentication events.
-
Save and close this catalina.properties file.
-
Restart the PamManagement service (Windows) or pammanager service (Linux) and wait 2-5 minutes for the service to come back online.
-
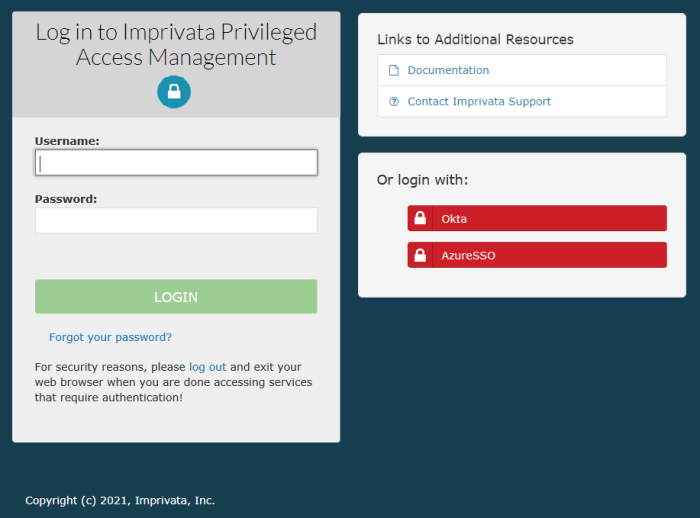
To check your work thus far, open your web browser and navigate to the PAM login page. If you see a red button labelled AzureSSO at the bottom right, please proceed to the next step. If you do not, please double check your configuration in the previous steps and restart the PAM service once more.
cas.managed.path={cas.managed.path}
cas.server.name={cas.managed.path}
cas.server.prefix={cas.managed.path}/cas
For users who installed and use PAM before 2021, the PAM root folder has the name xtam, so $PAM_HOME path will be for example c:/xtam/content/keys/azuresso.xml (Windows) or /opt/xtam/content/keys/azuresso.xml (Linux).
Please note, if you made changes around SSO parameters to the $PAM_HOME/web/conf/catalina.properties file with the previously generated .xml and .jks files, you need to regenerate those files to apply the new changes.
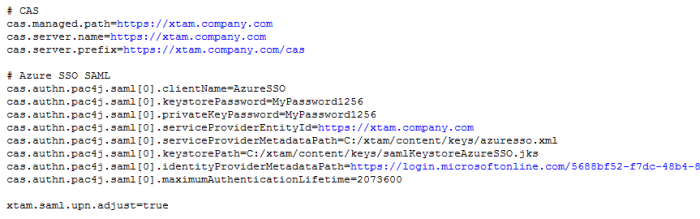
Please note, if PAM is configured to accept sAMAccountName logins as opposed to UserPrincipalName (UPN), then you will need to also add this line to this configuration file: xtam.saml.upn.adjust=true. Otherwise, when PAM is configured for UPN, you do not have to include this line or if you do, set it to false.
If you want to force a login every time for your users, you can add the following line to this configuration file:
cas.authn.pac4j.saml[0].forceAuth=trueFor Federated Sign In using PAM installation with CAS.V.6.x version:
open the file $PAM_HOME/web/conf/catalina.properties in a text editor, locate parameter to the section labeled # CAS, and add or update the following line:
cas.authn.pac4j.saml[0].useNameQualifier=false.
Step 3: Test the Integration
This final step is used to test the integration between PAM and your Azure Active Directory Enterprise Application.
- Open a new browser session (private or incognito) and navigate to the Imprivata Privileged Access Management login page.
- Located on the bottom right of this login page, you should see a new red button labeled AzureSSO or whatever value you entered for the client name earlier.
-
To test the integration, the following is expected:
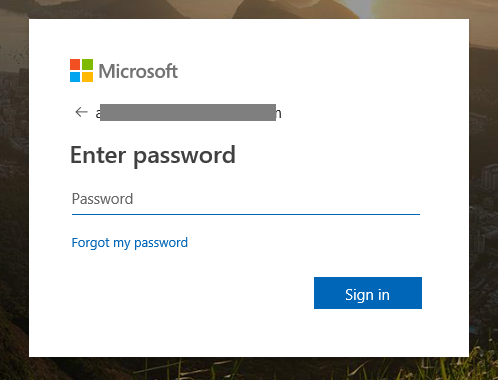
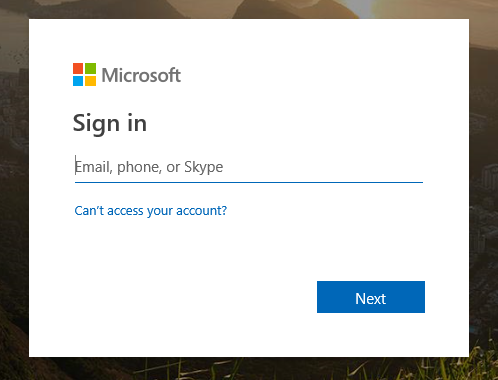
- When you click this red AzureSSO button, you will be redirected to the Microsoft Login page.
- You will enter your Azure Active Directory username that has been giving access to the Enterprise Application earlier and click Next.
-
You will enter the password for this user account and click Sign in.
-
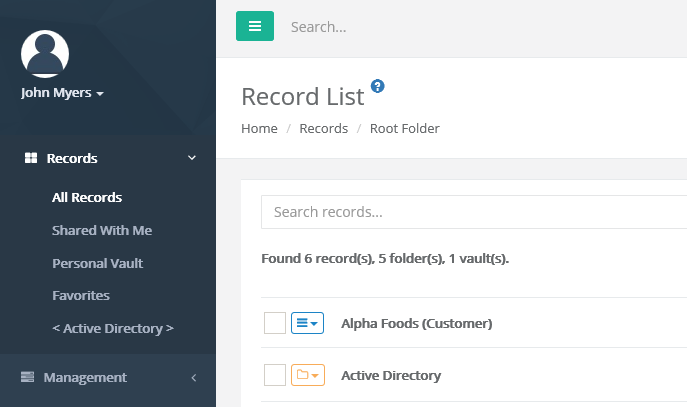
After the account is authenticated against Azure Active Directory, you will be redirected to the PAM homepage (All Records view) and your account should be displayed as logged in.

If you receive any errors during this test procedure, then recheck all configuration that was entered in the previous steps and restart the PAM service again.
To regenerate .xml and .jks files
-
On the PAM host computer, open the following file in a text editor $PAM_HOME/web/conf/catalina.properties locate the section labeled # CAS and specify the stated location for those files.
-
Remove or delete these previously generated .xml and .jks files from the location.
-
Restart PamManagement (Windows) / pammanager (Linux/Unix) service to regenerate those two .xml and .jks files, so your changes around SSO parameters can apply back to PAM.